Setting up MTA-STS
Note
This guide requires mailcow version 2025-09 or newer.
If manually setup before, be aware
If you previously configured MTA‑STS manually for your domain in mailcow, be aware any existing MTA‑STS files (for example .well-known/mta-sts.txt) are no longer reachable after this update. mailcow now serves MTA‑STS policies dynamically based on the domain's MTA‑STS setting in the UI and uses the configuration stored there.
mailcow does not create any MTA-STS files in the .well-known directory, all content is generated dynamically via PHP code.
Important
MTA-STS is particularly useful for domains that do not support (or cannot support) DANE. If you already use DANE (DNS-based Authentication of Named Entities), MTA-STS is not strictly necessary, but can be used in addition to further improve security.
What is MTA-STS?¶
MTA-STS (Mail Transfer Agent Strict Transport Security) is a security standard designed to improve the security of email transmissions. It allows domain owners to publish policies that require emails to be transmitted only over secure connections (TLS). This helps prevent man-in-the-middle attacks and ensures the integrity and confidentiality of email communication.
mailcow now supports managing MTA-STS policies directly through the mailcow UI, which was implemented as part of the "E-Mail-Sicherheitsjahr 2025" (Translates to "Email Security Year 2025") initiative of the German Federal Office for Information Security (BSI). mailcow actively participates in this initiative to promote general improvement of email security and make the configuration of those easier to accomplish.
Requirements¶
- mailcow version 2025-09 or newer
- A domain that points to your mailcow installation
- A valid SSL certificate for your domain (e.g. from Let's Encrypt)
- Access to your domain's DNS settings
Step 1: Enable MTA-STS in the mailcow UI¶
- Log in to the mailcow UI as an administrator.
- Navigate to E-Mail Configuration, followed by the Domains tab.
- Edit the domain for which you want to enable MTA-STS (click Edit).
- You should now see the MTA-STS tab, which looks similar to the following:
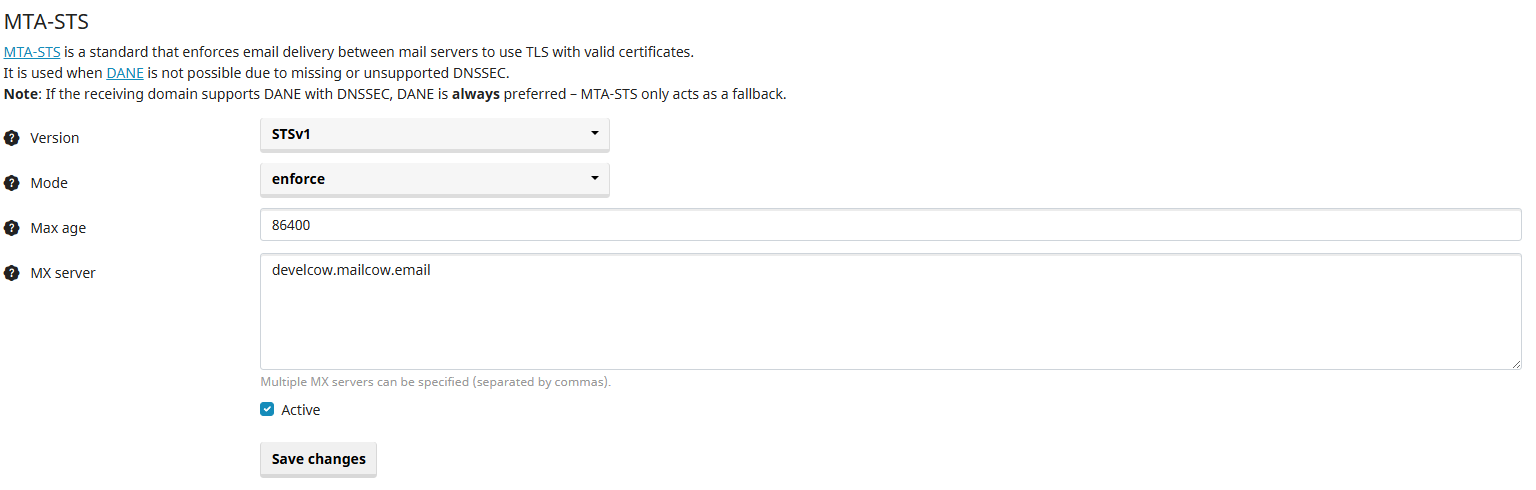
- Let's briefly go through all options:
- Version: The current version of the MTA-STS policy. Currently only version 1 (STSv1) is defined by the RFC standard.
- Mode: Choose the desired mode:
none: policy is disabled (monitoring only)testing: policy is active, but violations are only loggedenforce: policy is active and violations are blocked
- Maximum Age: Specify how long mail servers should cache the policy (in seconds). The recommended value is 86400 seconds (1 day).
- MX entries: Enter the MX records of your domain here, separated by commas. These records indicate which mail servers are authorized to receive email for your domain.
- After making the desired settings, check Active and click Save changes.
Step 2: Add DNS record for MTA-STS¶
- Create a new DNS TXT record for your domain with the name
_mta-sts.yourdomain.tld(replaceyourdomain.tldwith your actual domain). - The value of the TXT record should look like this:
v=STSv1; id=2024090101 v=STSv1: Indicates the version of the MTA-STS policy.-
id=2024090101: A unique identifier for the policy that should be incremented each time the policy changes (e.g. date of change in the format YYYYMMDDHH).Note
When changing the MTA-STS policy (e.g. changing the mode or the MX entries), the
idin the DNS record must be increased so that receiving mail servers recognize the new policy.mailcow automatically generates a new
idwhen you make changes in the mailcow UI and save them.You can always retrieve the currently valid id using the DNS Check within the mailcow UI (blue DNS Check button).
In general, after enabling MTA-STS in the mailcow UI you should always use the DNS Check to ensure that the DNS records (TXT and CNAME) are set correctly and have propagated.
-
Create another DNS CNAME record for your domain with the name
mta-sts.yourdomain.tldthat points to the mailcow FQDN (e.g.mail.yourdomain.tld, replacemail.yourdomain.tldwith your actual FQDN).Important
The CNAME record is required so that a valid SSL certificate can be generated (assuming mailcow generates the certificates) and receiving mail servers can retrieve the MTA-STS policy. mailcow hosts the policy file centrally to simplify management.
-
Wait for the DNS changes to propagate. This can take some time depending on the TTL settings of your DNS records.
Step 3: Verifying the MTA-STS configuration¶
- After the DNS records have propagated, you can verify the MTA-STS configuration.
- Use an online tool like Hardenize or the MTA-STS Validator from Mailhardener to check whether your MTA-STS policy is set up correctly.
- Alternatively, you can also use the DNS Check in the mailcow UI to ensure that the DNS records are set correctly.
Step 4: Monitoring and adjustments¶
- Monitor the email logs in the mailcow UI to ensure that no legitimate emails are being blocked.
- If you find that legitimate emails are being blocked, you can temporarily set the mode to
testingto log violations without blocking emails. - Adjust the MX entries and other settings as needed and increase the
idin the DNS record with every change. - Once you are confident that everything is working correctly, you can set the mode to
enforceto fully enforce the policy.